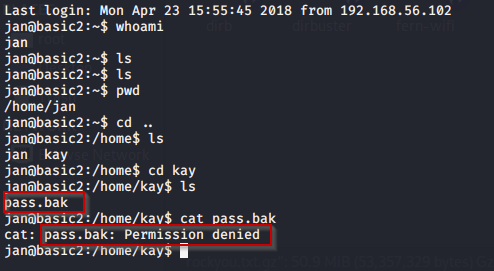
As the final project for a hands-on Penetration Testing course, I participated in a structured CTF-style assessment designed to simulate real-world offensive security scenarios. The challenge required enumeration, exploitation, and post-exploitation across multiple domains including Active Directory, web applications, and internal network services.

This project provided a complete end-to-end penetration testing experience—from reconnaissance to reporting—and sharpened my ability to think offensively while maintaining professionalism in documentation and communication.