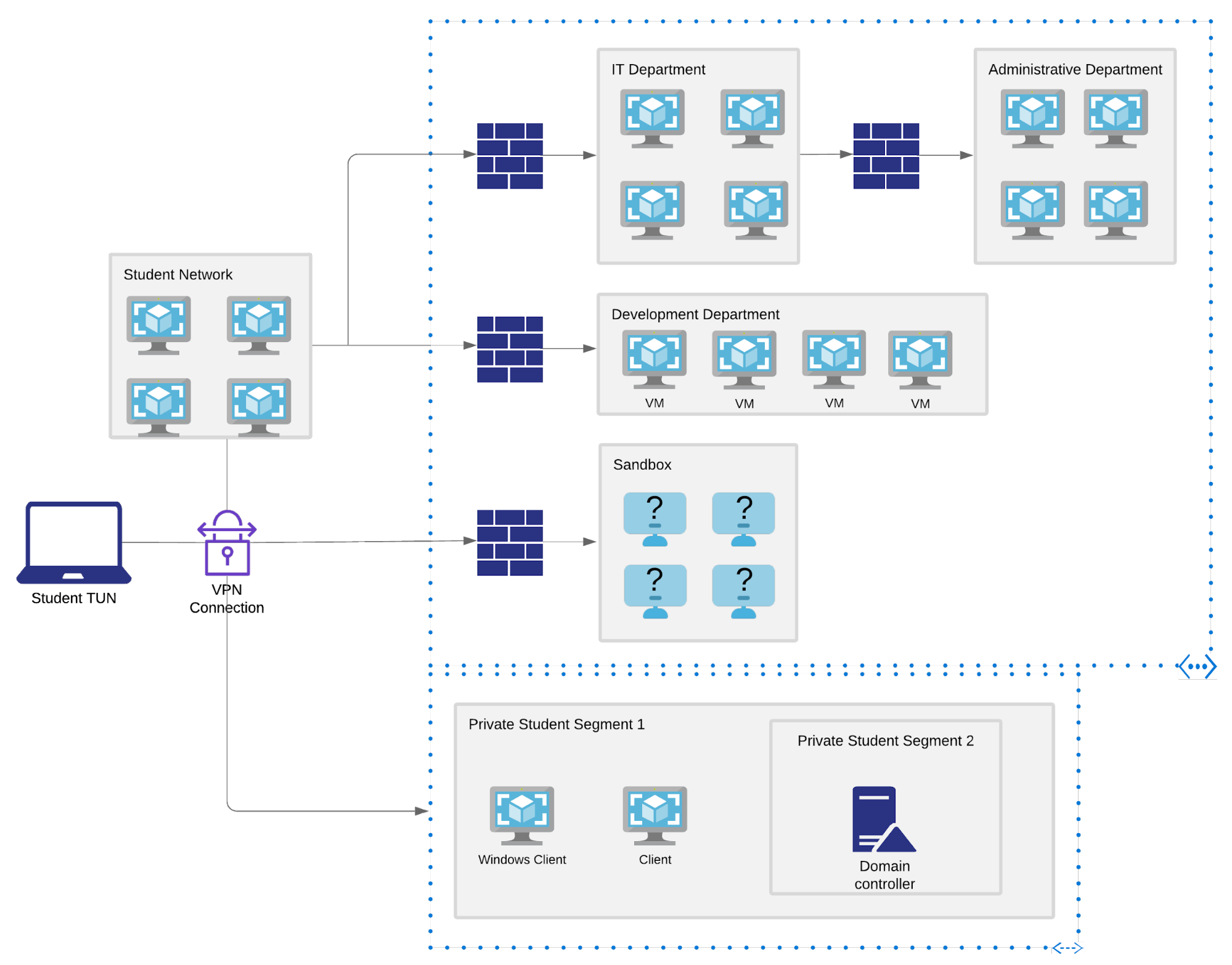
This course provided a comprehensive, hands-on introduction to securing cloud-based environments across IaaS, PaaS, and SaaS models. Through weekly exercises, platform-specific deep dives, and two major projects, I gained practical experience in securing applications, managing access, protecting data, and responding to incidents in the cloud.

Built practical skills in securing cloud applications, managing identity, protecting sensitive data, and responding to cloud-specific threats. Developed the ability to architect secure cloud environments aligned with compliance requirements and industry best practices.