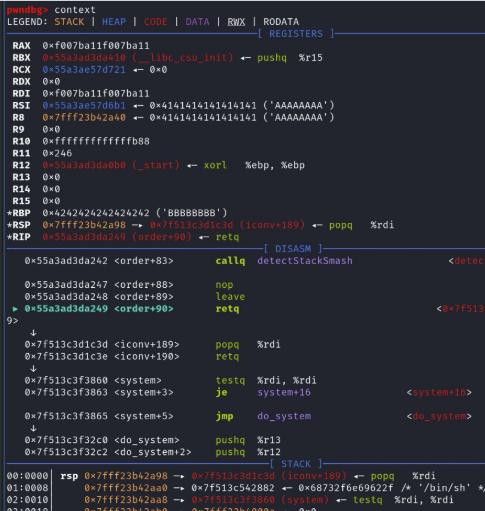
This course offered a deep technical dive into secure programming practices in C, with a strong focus on understanding how vulnerabilities arise at the assembly and memory level. Through hands-on demos and exploit development, I gained practical experience in writing secure C code and identifying common programming flaws that lead to critical security issues.
printf) to leak and manipulate memory.gdb and objdump to reverse, debug, and analyze behavior.gdb, pwndbg, and custom shellcode.
This course greatly enhanced my low-level security skills, making me more proficient in reverse engineering, exploit development, and secure C programming. It also reinforced a deep understanding of how software vulnerabilities are introduced—and how they can be prevented—right at the source.